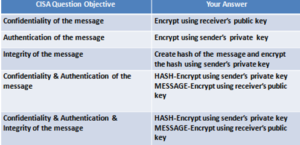
Point to remember for CISA exam-Asymmetric Encryption
(1)In any given scenario, when objective is to ensure ‘confidentiality’, message has to be encrypted using receiver’s public key.
(2)In any given scenario, when objective is to ensure ‘authentication’, HASH of the message has to be created and HASH to be encrypted using sender’s private key. Please note that hash is also known as message digest.
(3)In any given scenario, when objective is to ensure ‘integrity’, HASH of the message has to be created and HASH to be encrypted using sender’s private key. Please note that hash is also known as message digest.
(4)In any given scenario, when objective is to ensure ‘confidentiality & authentication’, following treatment is required:
-Hash of the message to be encrypted using sender’s private key (to ensure authentication/non-repudiation)
-Message to be encrypted using receiver’s public key (to ensure confidentiality)
(5)In any given scenario, when objective is to ensure ‘confidentiality & authentication & integrity’, following treatment is required:
-Message to be encrypted using receiver’s public key (to ensure confidentiality)
-Hash of the message to be encrypted using sender’s private key (to ensure authentication/non-repudiation and integrity)
(6)Below table summarizes the above provisions: