Point to remember for CISA Exam-Classification of Information Assets
(1)In any given scenario, following are the logical steps for data classification:
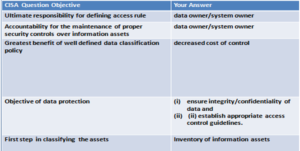
-First step is to have inventory of Information Assets.
-Second step is to establish ownership.
-Third step is classification of IS resources.
-Fourth step is labelling of IS resources.
-Fifth step is creation of access control list.
(2) In any given scenario, data owner/system owner is ultimately responsible for defining the access rules.
(3)In any given scenario, accountability for the maintenance of proper security controls over information assets resides with the data owner/system owner.
(4)In any given scenario, greatest benefit of well defined data classification policy is decreased cost of control.
(5)In any given scenario, most important objective of data protection is to (i) ensure integrity/confidentiality of data and (ii) establish appropriate access control guidelines.
(6)Data classification must take into account following requirements:
-Legal/Regulatory/Contractual
-Confidentiality
-Integrity
-Availability
(7)Following table summarize the above provisions: