(1)Types of Firewall
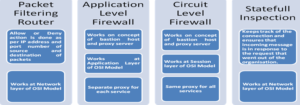
(2)Out of all types of firewall, Application-Level Firewall provides greatest security environment (as it works on application layer of OSI model).
(3)In any given scenario, most robust configuration in firewall rule is ‘deny all traffic and allow specific traffic’ (as against ‘allow all traffic and deny specific traffic’).
(4)In any given scenario, Stateful Inspection Firewall allows traffic from outside only if it is in response to traffic from internal hosts.
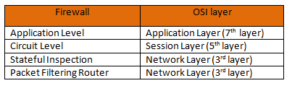
(5)In any given scenario, following are the OSI layers at which various firewall operates:
(6)What is bastion host?
Both Application-Level Firewall as well as Circuit-Level Firewall works on concept of bastion hosting. On the Internet, a bastion host is the only host computer that a company allows to be addressed directly from the public network and that is designed to protect the rest of its network from exposure. Bastion host are heavily forfeited against attack.
Common characteristics of a bastion host are as follows:
-Its Operating system is hardened, in the sense that only essential services are installed on it.
-System should have all the unnecessary services disabled, unneeded ports closed, unused applications removed, unnecessary administrative tools removed i.e vulnerabilities to be removed to the extent possible.
-It is configured to require additional authentication before a user is granted access to proxy services.
-It is configured to access only specific hosts.
(7)What is Proxy?
A proxy is a middleman. Proxy stands between internal and external network. Proxy will not allow direct communication between two networks. Proxy technology can work at different layer of OSI model. A proxy based firewall that works at lower layer (session layer) is referred to as circuit-level proxy. A proxy based firewall that works at higher layer (application layer) is called as an application-level proxy.